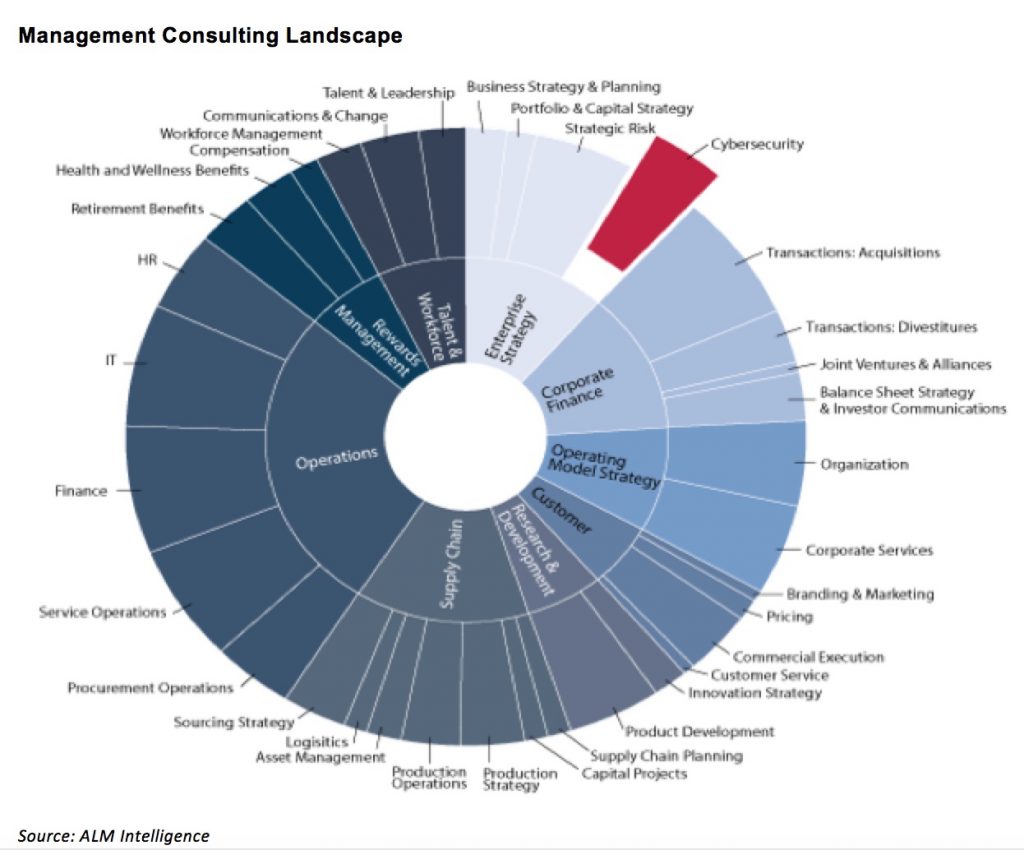
What is Cybersecurity Consulting?
ALM Intelligence views Cybersecurity consulting as a sub-set of Enterprise Strategy consulting with advisory focusing on delivering enterprise-wide cybersecurity strategies aligned with overall business strategies, while utilizing tools and technologies across functions to ensure that organizations are protected against cyber threats to information, infrastructure and applications. Importantly, this also includes establishing business processes, governance and infrastructure to best prevent and detect attacks and prepare for incident response and business continuity as needed.
To continue reading, become an ALM digital reader
Benefits include:
- Authoritative and broad coverage of the business of consulting
- Industry-leading awards programs like Best Firms to Work For, Global Leades and Rising Stars
- An informative newsletter that goes into the trends shaping the industry
- Critical coverage of the employee benefits and financial advisory markets on our other ALM sites, BenefitsPRO and ThinkAdvisor
Already have an account? Sign In Now